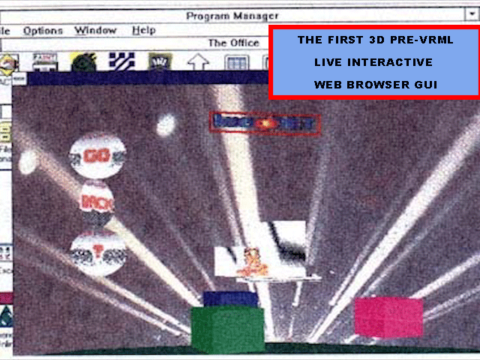
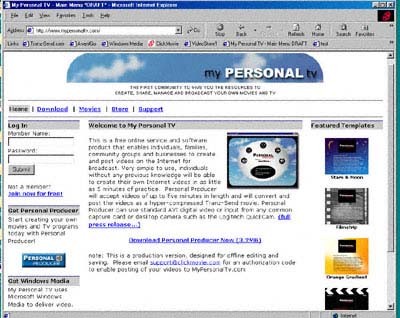
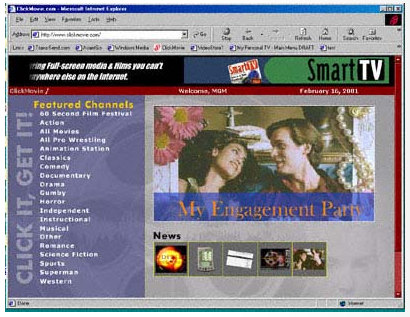
ARTICLES ABOUT PAST PROJECTS
PHOTO GALLERY OF PAST PROJECTS AND VENTURES
Click each image to see it larger.
PAST PROJECTS PHOTO ALBUM
PAST PROJECTS PHOTO ALBUM
- Please Wait For It To Load -
- Please Wait For It To Load -
PAST PROJECTS: TOPICS
- CONTACT
- CONTRIBUTE
- LUMIASCAPE PRESENTATIONS PRODUCED BY OUR TEAM
- OUR VIRTUAL REALITY (VR) AND FLIGHT SIM INVENTIONS AND PRODUCTS
- PAST CONSTRUCTION PRODUCTS AND PROJECTS
- PAST CONTENT CREATION AND ART DIRECTION
- PAST LOGISTICS AND OPERATIONS MANAGEMENT
- PAST MAJOR EVENTS AND PRESENTATIONS
- PHILANTHROPY AND COMMUNITY SERVICE PROGRAMS
- PRIVACY AND WEB SECURITY POLICY
- PROJECT VIDEOS OF PAST EFFORTS
- REFERENCES AND CREDENTIALS FROM PAST PROJECTS
- WEB SITE SECURITY NOTES